Built-in access control audit log#
Dell Data Analytics Engine, powered by Starburst Enterprise platform (SEP) maintains logs of all access attempts and access control changes
performed through its built-in access control functionality. When enabled, the
Audit log feature appears for members of the sysadmin role.
Note
The built-in access control audit log is in public preview. Contact Starburst support with questions or feedback.
The Audit log feature in the Starburst Enterprise web UI appears under the following conditions:
The cluster must have access control auditing enabled with
starburst.access-control.audit.enabled=truein the coordinator’sconfig.propertiesfile.The currently logged-in user must be assigned to the
sysadminrole, either in thestarburst.access-control.authorized-usersproperty or assigned in the built-in access control UI.The currently logged-in user must be switched to the
sysadminrole.
To access the audit logs, click Security > Audit log. Audit logs are subject to the Insights data retention configuration.
The following audit logs are available:
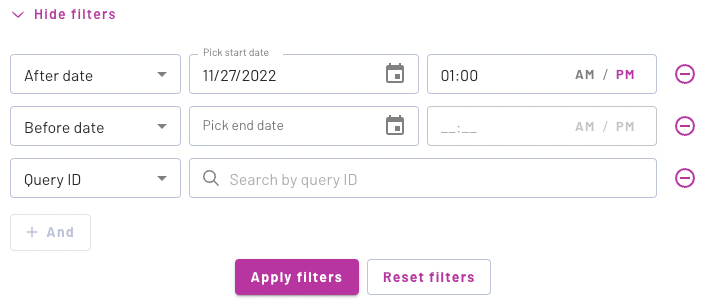
Filters#
The Audit log page includes filters by date and time range as well as query ID:
After date - Selects the start date and time of the filtered results.
Before date - Selects the end date and time of the filtered results.
Query ID - Selects a query ID, which can be found for example on the Insights Query overview page.
By default, the filter UI controls are hidden. Click Show filters to expand the filter section. Click Hide filters to collapse the filter section. The filter criteria is still visible when collapsed.
The After date (start date) filter is always available by default, and is set to the date one day (24 hours) prior to the current date. Click the + And button to add another filter. To remove a filter, click the minus - button by the filter. The After date filter cannot be removed.
You can adjust the date and time for the before and after filters. The default
time for the After date filter is 12:00 AM. The default time for the
Before date filter is 11:59 PM.
Warning
Log files can quickly grow to a very large size depending on the size of an organization and its level of activity. For that reason, the default filter setting for downloading a log file is 24 hours. Broaden or narrow the date range as appropriate by adjusting the filters.
Click Apply filters to filter the audit logs. Click Reset filters to revert the After date filter to its default and remove all other filters.
The Audit log provides infinite scrolling so you can conveniently view the incoming audit records according to your selection criteria.
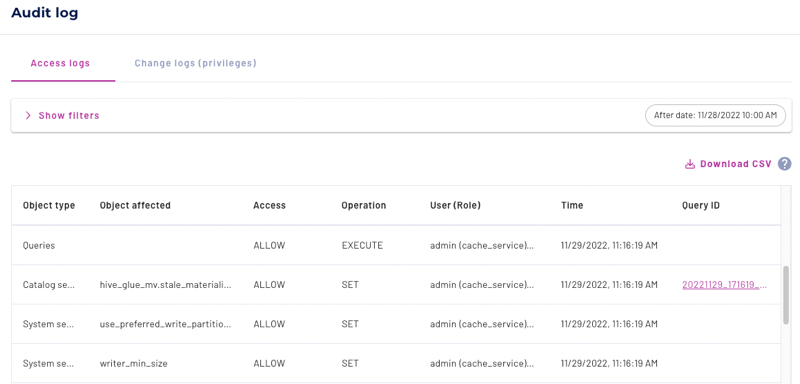
Access logs#
The access logs allow data administrators the ability to see the access details of objects secured by access control.
Enable the access logs#
The access logs are disabled by default. To enable the access logs, set the
starburst.access-control.audit.access-log.enabled configuration
property in the cluster’s config.properties file to true.
To disable the access logs, set the property to false. Disabling the
access log hides the Access logs tab.
Access log configuration#
The following configuration properties are available:
Property |
Description |
|---|---|
|
Enables the Access log tab in the Audit log page. Set to |
|
Sets the size of the access log queue by the number of queued events.
Default: |
Warning
If the access log queue becomes full, all queries fail with the
message that the access log queue is full. You can increase the queue
size using the starburst.access-control.audit.access-log.queue-size
configuration option.
Access log records#
Each record in the Access logs tab includes the following columns:
Object type - The type of object that was accessed. Object types include Tables, Queries, Audit logs, System sessions, and Catalog sessions.
Object affected - The object that was affected by being accessed. This is typically populated for a query execution.
Operation - Operation performed such as
SET,SELECT,CREATE,SHOW, orEXECUTE.Access - The access level of the operation, such as
ALLOW,DENY.User (Role) - The user who made the change, and the role that they used to make the change.
Time of change - Date and time in the local time zone that an object was accessed or access was attempted.
Query ID - The ID of a query.
Query details - For query operation entries, a link that goes to the Query details page for that operation.
Download the access logs#
Download the access control access log as a comma-separated values (.csv)
file that contains all of its records for unfiltered data, or only for the
filtered results if filters were applied.
Click Download CSV in the Starburst Enterprise web UI Audit log page Access logs tab.
Example downloaded output:
Id,Action,EntityCategory,Entity,EntitySpecified,GrantOption,AccessResult,User,Roles,QueryId,TimeOfChange
11762713,SHOW,Audit logs,,false,false,ALLOW,alice,[sysadmin],,2022-10-20T13:56:10.915174Z
11762712,SHOW,Audit logs,,false,false,ALLOW,alice,[sysadmin],,2022-10-20T13:56:02.841578Z
11762711,SHOW,Queries,,false,false,ALLOW,alice,[sysadmin],,2022-10-20T13:56:00.139609Z
11762710,SHOW,Audit logs,,false,false,ALLOW,alice,[sysadmin],,2022-10-20T13:56:00.138180Z
11762709,SHOW,Audit
logs,,false,false,ALLOW,alice,[sysadmin],,2022-10-20T13:56:00.136584Z
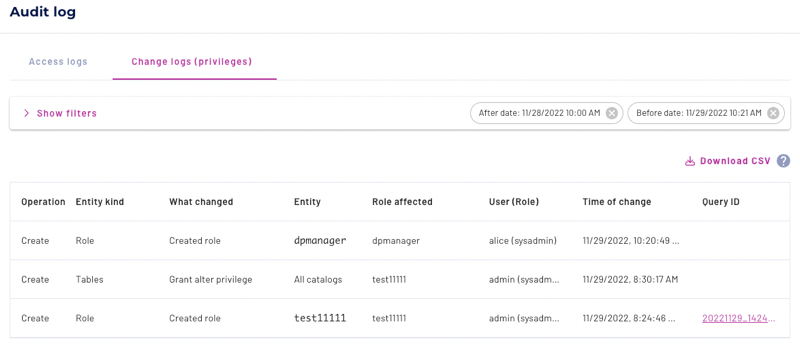
Change logs (privileges)#
The change logs allow data administrators the ability to see role and privilege changes made using built-in access control.
Change logs records#
Each record in the Change logs tab includes the following columns:
Operation - Operation performed such as Create, Assign, or Delete.
Entity kind - Type of entity such as Role, User, or Privilege.
What changed - A description of the state change, such as Created Role, Grant select privilege, Deny drop privilege, and so on.
Entity - The entity affected, such as All catalogs, All data products and domains, or a more specific entity.
Role affected - The role that the change was applied to.
User (Role) - The user who made the change, and the role that they used to make the change.
Query ID - The ID of a query.
Time of change - Date and time in the local time zone of the change that was made.
Download the change logs#
Download the access control change log as a comma-separated values (.csv)
file that contains all of its records for unfiltered data, or only for the
filtered results if filters were applied.
Click Download CSV in the Starburst Enterprise web UI Audit log page Change logs tab.
Example downloaded output:
Id,Operation,EntityKind,WhatChanged,Entity,EntitySpecified,GrantOption,RoleAffected,User,Roles,QueryId,TimeOfChange
1515,Create,Role,Created role,dpmanager,true,,dpmanager,alice,[sysadmin],,2022-11-29T16:20:49.495895Z
1514,Create,Tables,Grant alter privilege,All catalogs,false,,test11111,admin,[sysadmin],,2022-11-29T14:30:17.373399Z
1513,Create,Role,Created role,test11111,true,,test11111,admin,[sysadmin],20221129_142445_10964_5c2mj,2022-11-29T14:24:46.032268Z